Sherlock Category: DFIR
Sherlock Difficulty: Medium
Scenario: Gladys is a new joiner in the company, she has received an email informing her that the IT department is due to do some work on her PC, she is guided to call the IT team where they will inform her on how to allow them remote access. The IT team however are actually a group of hackers that are attempting to attack Forela.
Task 1
Question: What was the name of the executable that was uploaded as a C2 Agent?
We have been provided with a KAPE Triage of the system, which contains several critical artifacts that can assist in solving the upcoming questions. Specifically, within the Windows Event Logs, there is key information regarding Windows Defender detections that could reveal the uploaded C2 agent. By examining the relevant entries in the Windows Defender event log, we can extract significant details, such as flagged executable files, associated detection IDs, and threat actions taken by the system.
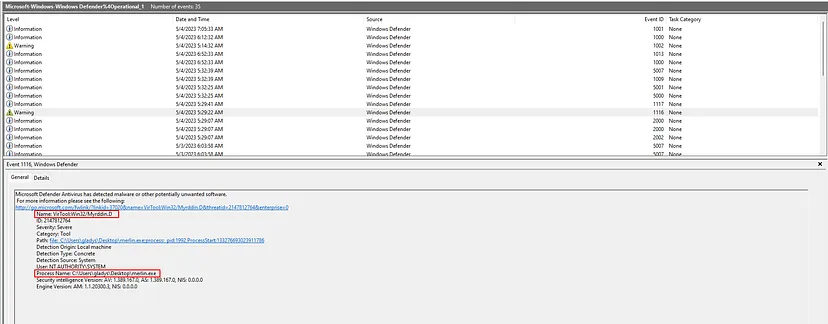
merlin.exe
Task 2
Question: What was the session id for in the initial access?
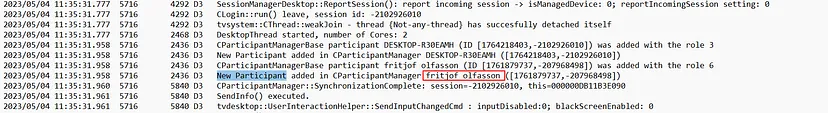
To identify the session ID used during the initial access, we can navigate through the provided TeamViewer logs. TeamViewer is a remote access and control software that allows users to securely connect to and manage devices remotely. By examining these logs, we can pinpoint the moment a connection was established. As shown in the log excerpt, the session ID -2102926010 was recorded when a remote connection attempt occurred, indicated by the log entry for the SessionManagerDesktop that highlights an incoming session connection.
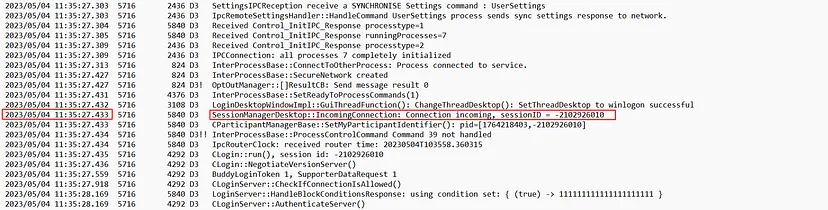
-2102926010
Task 3
Question: The attacker attempted to set a bitlocker password on the C: drive what was the password?
To determine the password used by the attacker when attempting to set BitLocker on the C: drive, we can analyze the Windows Event Logs, particularly focusing on Sysmon and PowerShell activities. By reviewing the logs, we identified a PowerShell command executed by the attacker, which is associated with BitLocker operations.
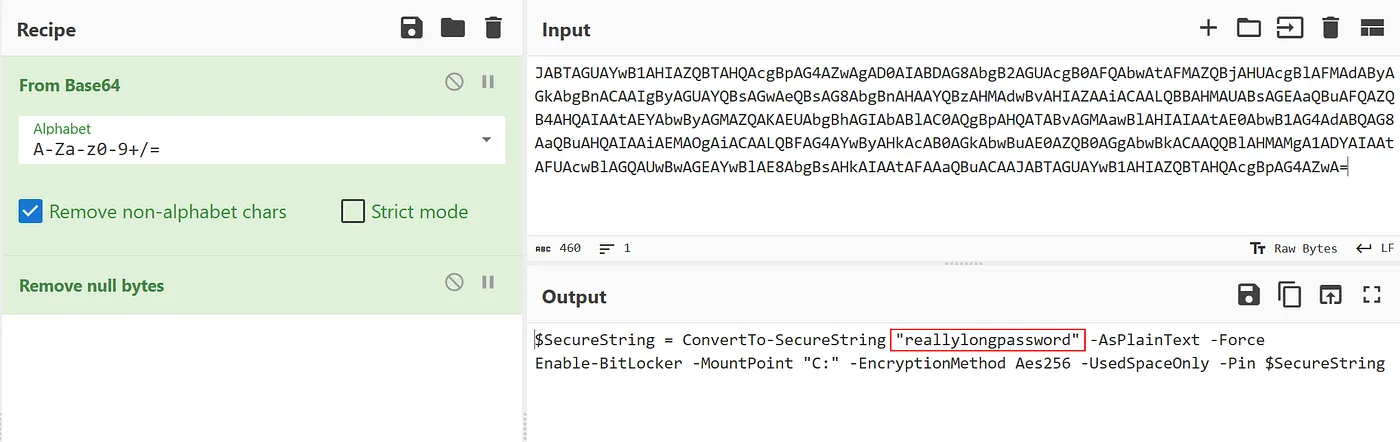
reallylongpassword
Task 4
Question: What name was used by the attacker?
By reviewing the TeamViewer logs, we can identify the name used by the attacker during the remote session. The logs reveal that the attacker utilized the name “Fritjof Olafsson” when connecting to the system.
Fritjof Olfasson
Task 5
Question: What IP address did the C2 connect back to?
To track C2 communication, we can streamline our investigation by filtering Sysmon logs for Event ID 3, which specifically captures network connection events.
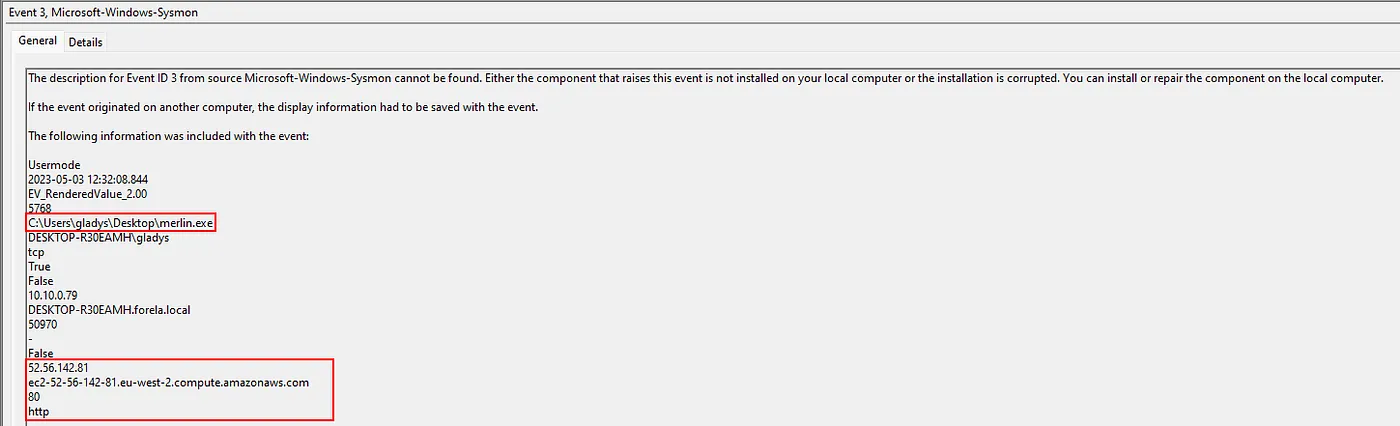
52.56.142.81
Task 6
Question: What category did Windows Defender give to the C2 binary file?
This was seen back in TASK #1, it was given the category “VirTool:Win32/Myrddin.D”
VirTool:Win32/Myrddin.D
Task 7
Question: What was the filename of the powershell script the attackers used to manipulate time?
This PowerShell script can be found alongside merlin.exe inside of the user gladys Desktop directory:
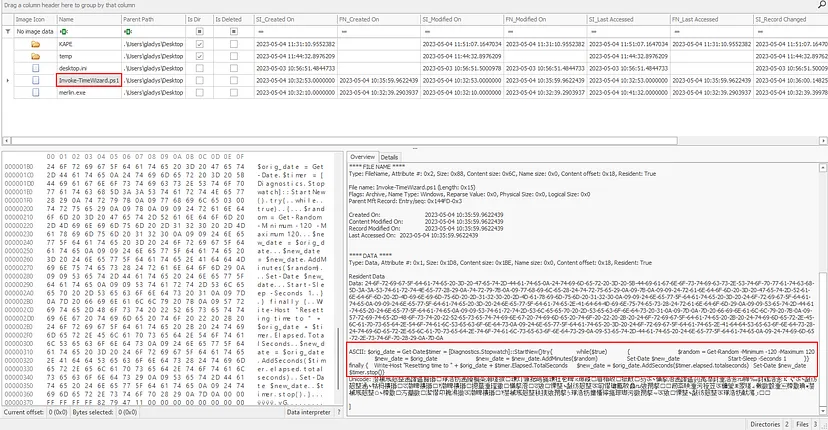
Additionally, and more practically, we can find the user’s PowerShell command history @ gladys\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline
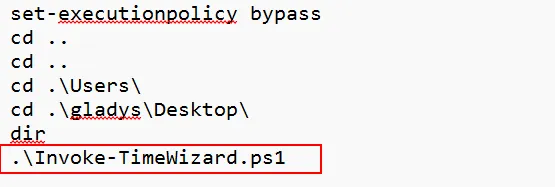
Invoke-TimeWizard.ps1
Task 8
Question: What category did Windows Defender give to the C2 binary file?
This can be seen from TASK #2
2023/05/04 11:35:27
Task 9
Question: What is the SHA1 and SHA2 sum of the malicious binary?
By examining the Windows Defender logs, we can extract critical information about the malicious binary, including its SHA1 and SHA2 hashes. C\ProgramData\Microsoft\Windows Defender\Support
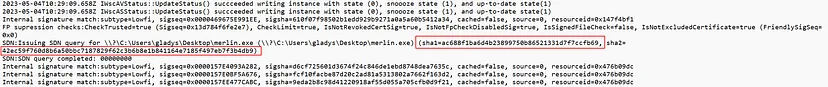
ac688f1ba6d4b23899750b86521331d7f7ccfb69:42ec59f760d8b6a50bbc7187829f62c3b6b8e1b841164e7185f497eb7f3b4db9
Task 10
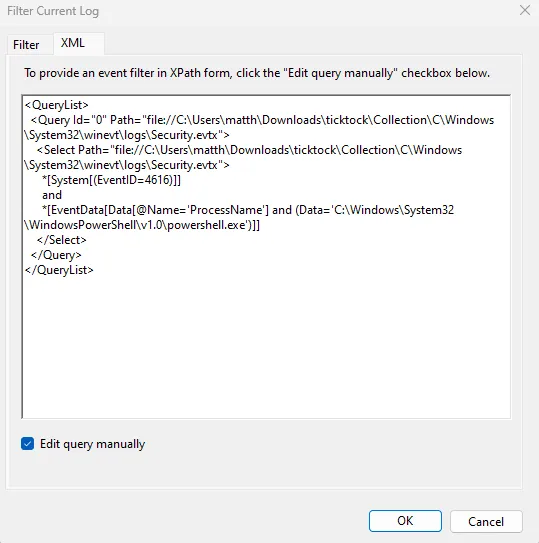
Question: How many times did the PowerShell script change the time on the machine?
We can turn to the security logs and notice the event ID 4616 (Security State Change). Specifically, this event is logged whenever the system time is changed in a Windows environment, so we can filter for this event code and specifically making sure it was Powershell.exe causing this system time change.
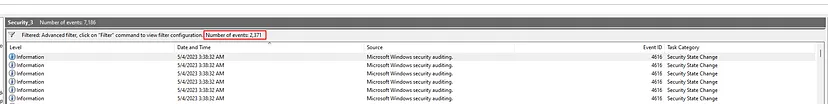
2371
Task 11
Question: What is the SID of the victim user?
In our security logs, we can look for any event involving the compromised user “gladys” to find their SID.
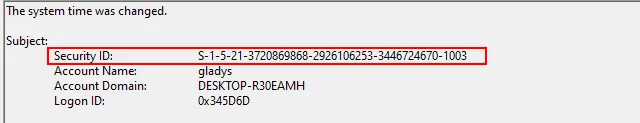
S-1–5–21–3720869868–2926106253–3446724670–1003